Latest Posts
-
Homelab | Gitea Actions with Terraform
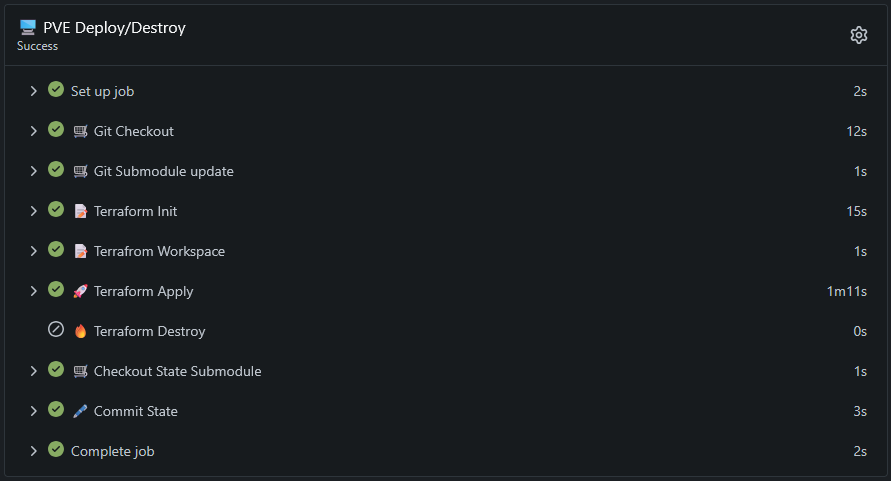
So, I wanted to be able to automate tasks in my homelab with Terraform and Ansible without ever having to git clone or having the binaries locally. Another thing I hated was dealing with Terraform state files. I use various machines and not having the state file can be a pain if you wanted to […]
-
Active Directory Lab | Emulating a phished user click
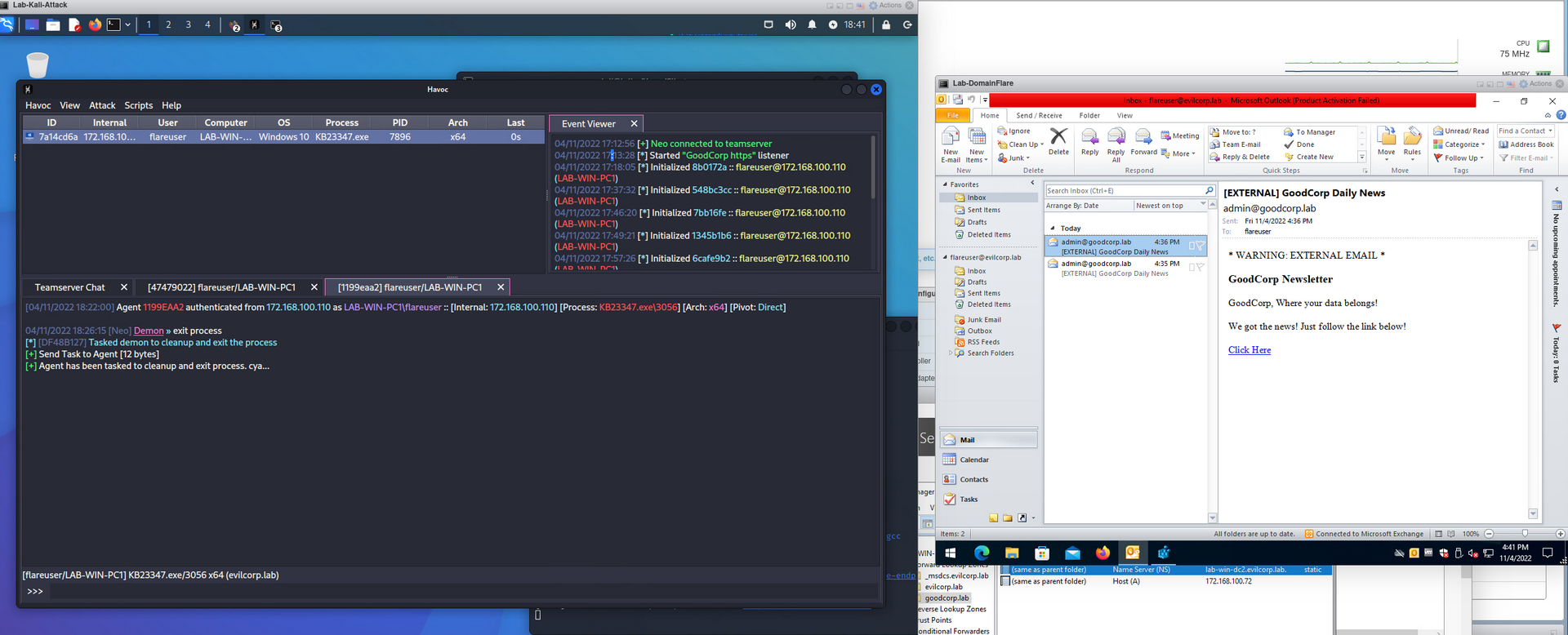
This is an attempt to emulate successfully phishing a user to the point in which they download and execute a payload. When doing things in a lab, it almost never emulates real user interaction and it is an extra step to login to the victim host just to click on an email you sent 30 […]
-
Linux Libvirt Build Pipeline
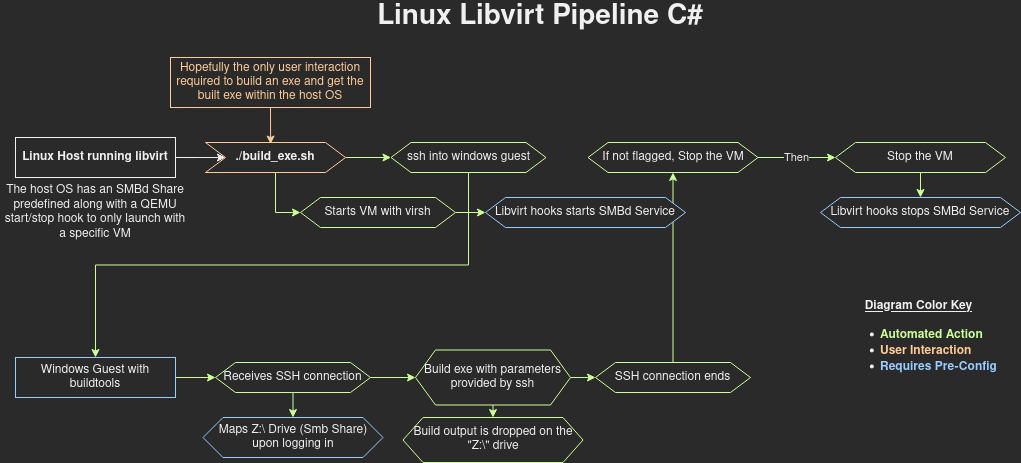
As a red teamer, I’ve needed to build various Windows executables that usually required me interacting with a Virtual Machine where I had to run Visual Studio or powershell to build the projects. If I was using VMware workstation or VirtualBox I could mount a local folder to store the files and what not but […]
-
PDF Captcha Phishing/Malware Analysis | Bitter-Shadow
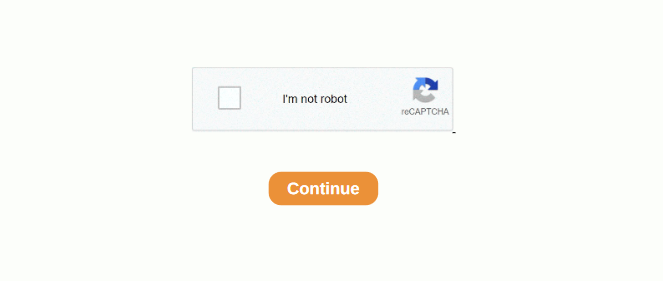
If you have google’d anything lately, you may have noticed an increase in squarespace/cdn PDFs that resemble google Captchas. Most of these documents contain a fake captcha, wall of text and a series of PDF links to have random subject names on every type of top level you can think of.
-
MalwareTech Challenge | Strings1
At this point in my career I have had the chance to analyze various forms of malware, but I still have yet to dive deep into reversing from assembly. I understand the basics and have analyzed some of my own basic C programs but I always feel like I am missing something or it was […]
-
WriteUp | HTB | Jerry
Out of all of my HTB experience. Jerry was one of the easiest. However, that doesn’t mean it wasn’t fun. I took the opportunity to use some tools I hardly or have never used.