At this point in my career I have had the chance to analyze various forms of malware, but I still have yet to dive deep into reversing from assembly. I understand the basics and have analyzed some of my own basic C programs but I always feel like I am missing something or it was too easy because I made it and understood what I was looking for.
In an attempt to find challenges, I attempted a few of HackTheBox’s Reversing challenges but after Googling around, I found MalwareTechBlog’s challenges. I have followed this guy for a while on twitter and never knew he released reversing challenges.
In an attempt to learn how to reverse, I am gonna be going through his challenges.
Challenge Information provided is as follows:
strings1.exe contains an un-encrypted flag stored within the executable. When run, the program will output an MD5 hash of the flag but not the original.
Rules & Information
– You are not require to run strings1.exe, this challenge is static analysis only.– Do not use a debugger or dumper to retrieve the decrypted flag from memory, this is cheating.
– Analysis can be done using the free version of IDA Pro (you don’t need the debugger).
https://www.malwaretech.com/strings1
What I am expecting is an elaborated program that runs along the lines of:
int main() {
string password="password123";
string password_md5=md5.hexdigest(password);
printf("%s\n", password_md5);
return 0;
}
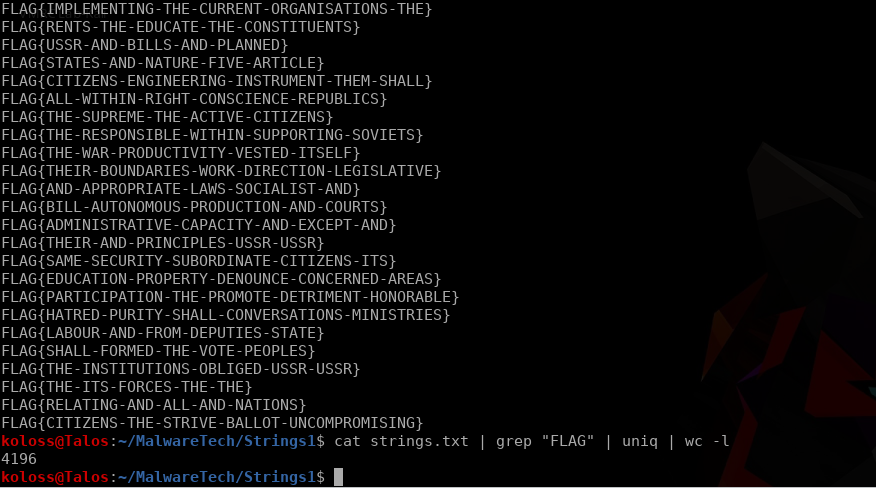
My first approach was basic, used previously on other executables for things like hard coded passwords for privesc in HTB. I ran strings and was greeted with a glorious set of fake flags. 4,196 unique “Flag” strings.
This approach was definitely not fruitful so I decided to launch Ghidra. I am still learning Ghidra and due to the fact that it has the Convert to code function built in and it’s free. It seems like the best choice. My first step was finding the md5 function which luckily was identified as ‘md5_hash’ in the symbol tree. First look at this appears to be rather simple. It is a function that accepts a char parameter and returns chars after processing it through the digestString/MD5 Function.
char * __cdecl md5_hash(char *param_1)
{
char *pcVar1;
pcVar1 = digestString((MD5 *)&DAT_004331d0,param_1);
return pcVar1;
}
Next I used the context menu to look for all references to md5_hash. This showed only one CALL at 0x004022BA. Just above the call instruction, you can see a MOV EAX, PTR_s_FLAG*, showing the reference to the string used in the call of md5_hash.
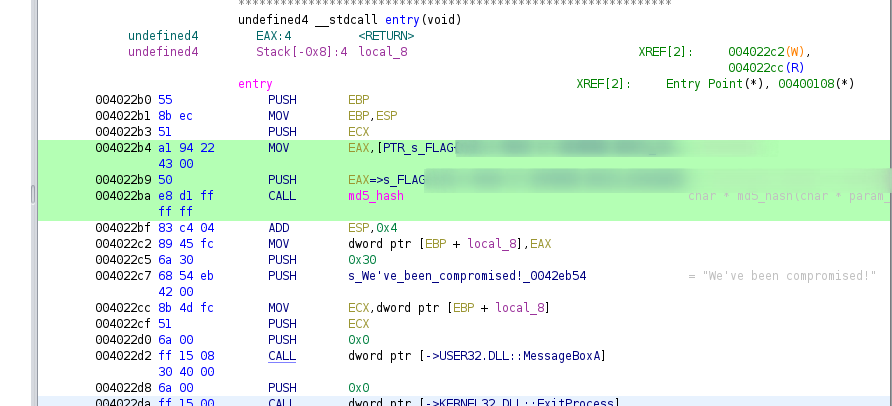
Double clicking the reference on the PUSH instruction takes you to the referenced string where you can copy it out and check the if the flag is correct on the site to get the “Correct Flag!” page.
Although extremely simple. I feel like it is at least useful to start using a new tool like Ghidra.