So, I wanted to be able to automate tasks in my homelab with Terraform and Ansible without ever having to git clone or having the binaries locally. Another thing I hated was dealing with Terraform state files. I use various machines and not having the state file can be a pain if you wanted to update or destroy a Terraform deployed host. There have been a couple of projects like Gaia that handle state files and Terraform deployment but it has died like many similar projects. You can use a remote state file provider but most of those require enterprise/cloud solutions like S3 and running Minio for just state files feels clunky. Very few options are even available for homelab/self-hosted use.
Continue reading “Homelab | Gitea Actions with Terraform”Tag: Homelab
Active Directory Lab | Emulating a phished user click
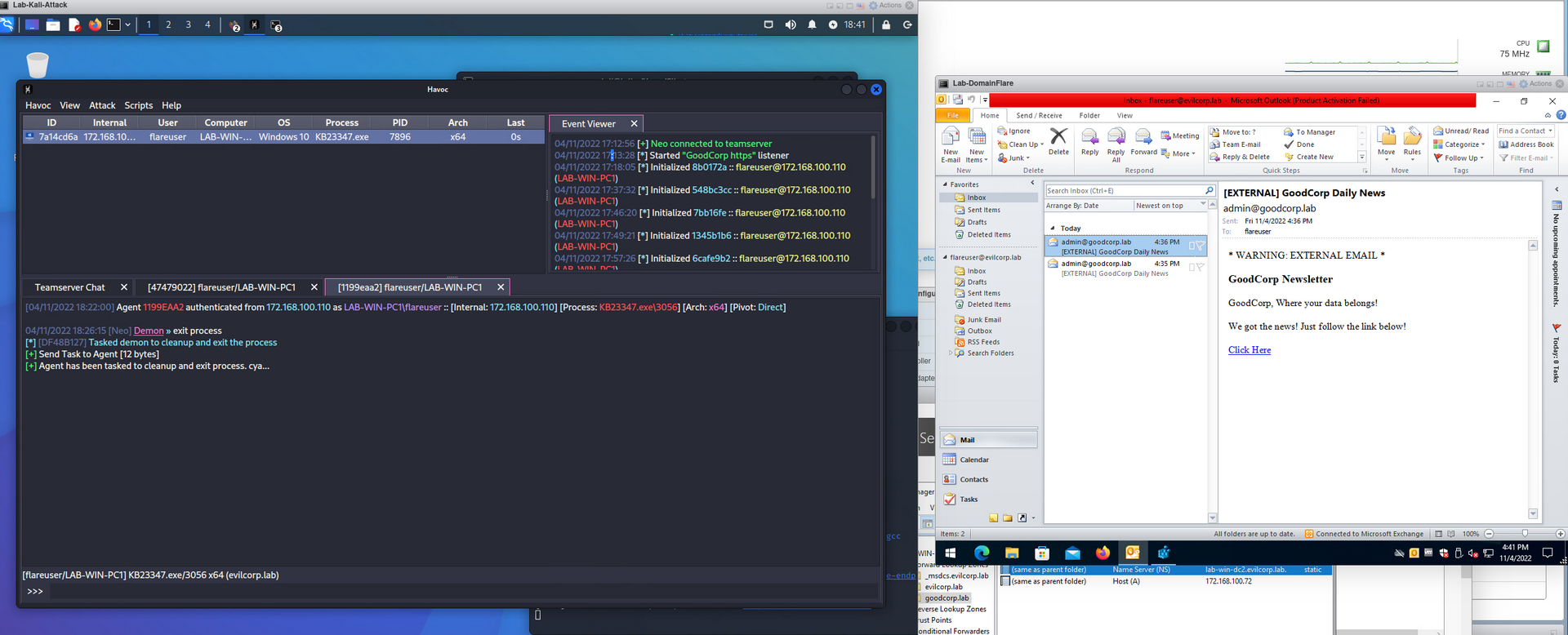
This is an attempt to emulate successfully phishing a user to the point in which they download and execute a payload. When doing things in a lab, it almost never emulates real user interaction and it is an extra step to login to the victim host just to click on an email you sent 30 seconds ago. This method uses outlook rules and powershell to automatically download and execute a link received from a specific user.
This isn’t exactly a full tutorial with every command and button click, more of the steps I went through to create the emulated actions.
Continue reading “Active Directory Lab | Emulating a phished user click”